A wolf in a sheep’s clothing is still … well, a wolf. What comes to mind when you think of this metaphor? For us, it’s the many scammers who try to access your information by appearing as legitimate email business messaging.
Phishing is one of the most common forms of social engineering (fraud that involves hacking people to obtain information), and about 96% of social engineering is done through phishing emails. You may have noticed that October was Cyber Security Awareness month, but cyber frauds go on all year long. Here are some tips to help you avoid falling victim to a phishing scam.
The Link Will Make You Think
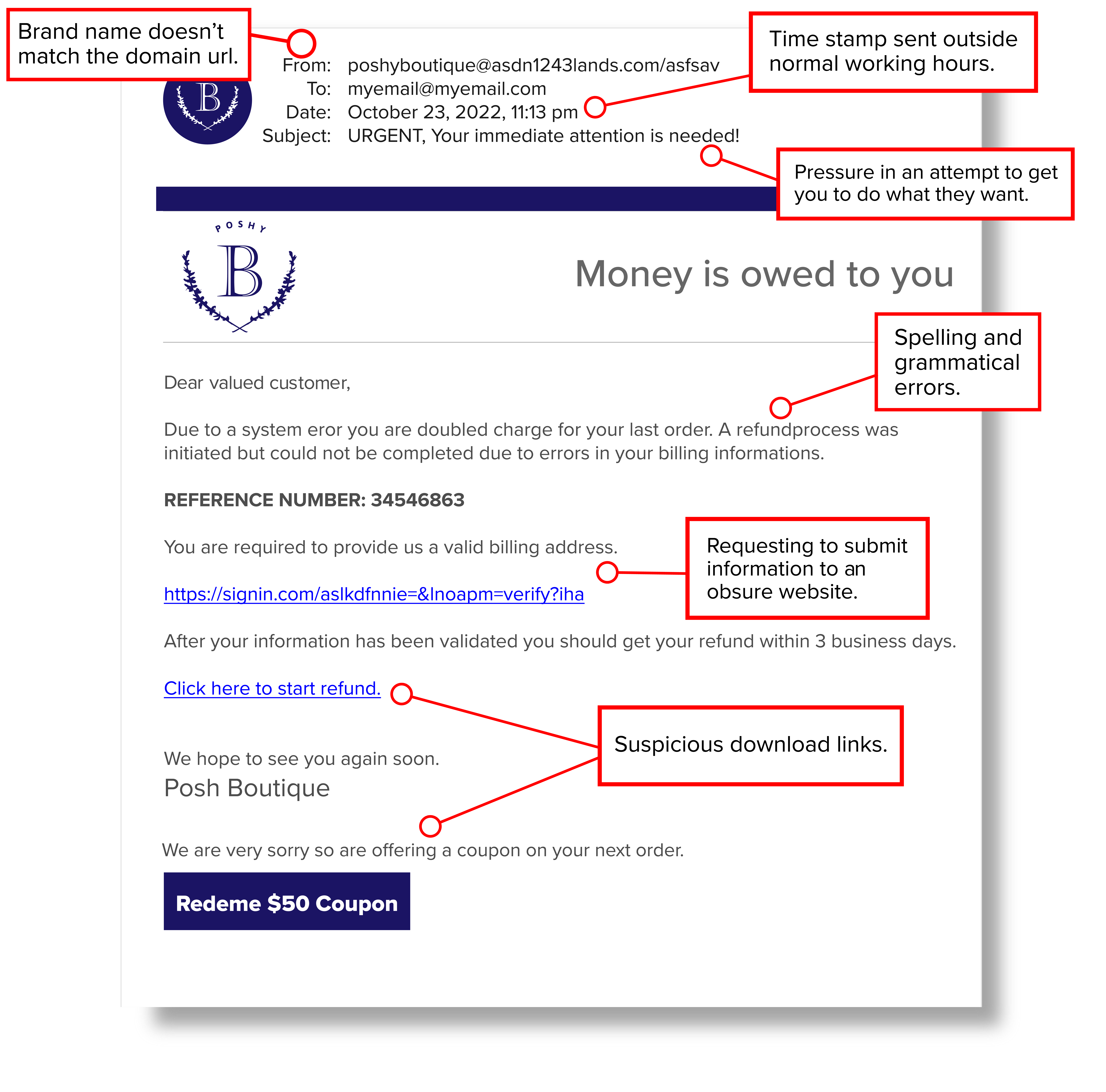
A general rule of thumb would be to never click on links, but we know it’s not always that easy. Here are a few ways to tell if something might be “phishy” about an email link:
- Something is misspelled in the link to a website or brand. Cyber scammers aren’t the BEST spellers, and fortunately, it’s easy to spot if you know where to look.
- The brand name may check out, but take a look at the domain to determine if it’s real or not. You should also be weary if the brand name is in the email address or URL, but it doesn’t match the domain.
- Overly long, OR overly short URLs. URLs that contain 100 or more characters, for example, are attempts at obscuring the true domain and/or linking to a completely different website at the end.
If you’re still unsure, you can always do your own research to find the legitimate website. You can also hover your mouse over links in the email to see if they will lead you to an unexpected website. Just don’t click!
Grammar Gives it Away
Grammatical errors are a clear giveaway. Legitimate emails are professionally written and usually checked for typos or structural errors. Even if it looks clean, compare the consistency with previous emails you’ve received from the company. Pay close attention to how they address you as well. If they say “Dear Little Red Riding Hood,” they’re clearly a wolf in disguise! A scammer may address you as a valued customer, while a legit company or coworker will use your name or a simpler greeting such as “hello.”
Urgency is Never Necessary
A scammer is going to lay on ALL the pressure in an attempt to create panic and get you to do what they want. Language that invokes urgency, like “failure to do so in 24 hours will lead to account suspension” or “Immediate action required/it is very important that you follow these directions or else…” are threats that legitimate companies are less likely to use. These scams can also claim that you’ve already been hacked, or your information is at risk, and give you instructions to “protect” yourself. But beware – this is just a disguise to confirm your personal information and a telltale sign of an imposter. Another form of urgency can appear in the subject line. An alarming subject line will get you to act fast – before you even have time to think or outrun the predator.
What If All This Checks Out? Well, There’s More!
Here are a few extra things you can look for in a phishing attempt:
- To, From, and Reply lines – are there people you don’t know included in the email? Are you able to verify the email addresses? Do the From and Return addresses match? Scammers are most believable when impersonating someone you trust, like your company’s payroll. But watch out!
- Don’t go on a date with the wolf – look at the date line and time stamp of the email and make sure it wasn’t sent at an odd time, or outside of normal work hours.
- You should even be cautious about personalized emails. This is one of the ways “phishing” emails have gotten trickier, and it’s called spear phishing. Remember – every piece of public information is also accessible to bad people, and they can use it against you.
- Don’t click on downloads or attachments if you aren’t expecting them! Even if it’s to avoid “negative consequences.”
If all of this is a little overwhelming (because it absolutely can be!), check out the infographic below for a list of example scenarios to look for in phishing attempts.
Arm yourself with the information to protect against cyberattack attempts delivered to your email. Be on the lookout, it’s okay to be skeptical, and run through this checklist to avoid falling victim to email phishing scams.
Want more resources on cyber security and information safety? Visit Moneytree’s Staying Secure Page.
